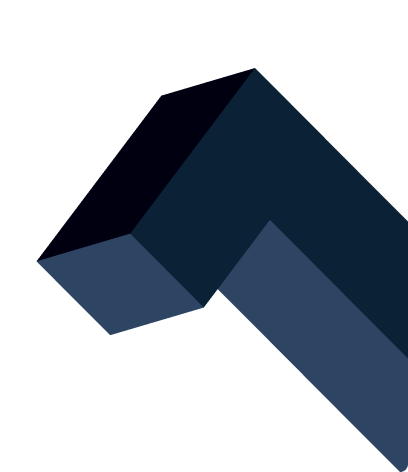
Secure meetings with complete data control
A self-hosted and secure video conferencing solution that can be used in any meeting room or on any device.

Modern
UX
Customizable
platform
Easy
setup
Reliable
performance
Advanced
security
Privacy, control, and compliance drive the need for secure meetings
Manage risk and compliance with robust protection standards tailored to every industry.
Compliance & data control
Adhere to data sovereignty requirements by ensuring data transfer and storage align with local regulations. By self-hosting the deployment, you can be confident that your data remains your data.
User access & authentication
Use advanced authentication to ensure only the right people attend the right meeting at the right time. Grant access based on attributes like role, device type, location, and IP address.
Redundancy & backup
Implement resilient video meetings as part of your business communication plan, whether to comply with regulations such as NIS2 or to ensure uninterrupted access to a collaboration platform.
Business continuityZero trust architecture
Adhere to zero trust principles by enforcing continuous identity and integrity verification for all users and devices, irrespective of location, and implementing stringent access controls and authentication measures.
Zero trust architectureA modern platform
Pexip Secure Meetings is a self-hosted video conferencing solution. Designed to run in private or sovereign clouds, or on-premises. The solution is easy to install, manage, and scale – you can be up and running in a couple of hours.
Trusted by


Your secure meeting alternative
catering to restricted meetings that require privacy and control.
Easily book secure meetings
Secure Scheduler for Exchange
Secure Scheduler for Web
Ensure your security & privacy requirements are met with a self-hosted meeting platform
Build trust through a familiar branded interface
Create a personalized user experience
Ensure that the right person attends the right meeting
Leverage your identity provider of choice
Ensure only authorized and identified individuals enter a meeting.
Integrate with identity providers, like Google, Microsoft, or Okta for secure access.
Authenticate users through Single Sign-On protocols such as SAML 2.0 and Open ID connect (OIDC) for easy, secure logins.
Kick authentication up a notch
Pexip's access control uses a policy server with Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) for security and customization.
It assigns access by roles (RBAC) and fine-tunes permissions with ABAC, ensuring precise control and protection of sensitive resources.
Encourage situational awareness
Create security awareness
Integrate and customize solutions
Harness our APIs and SDKs for your platform
Leverage our comprehensive APIs and SDKs to:
- Tailor the platform to your specific needs, including user interface design and functionality
- Integrate with existing systems and workflows
- Conform to your unique security requirements – our definition of security is your definition of security
You own all data associated to your meetings
Your data is your data
In shared cloud solutions you don't get to know where your data goes. Maintain complete control over the routing, storage, and handling of your video traffic, including associated data and metadata such as call detail records, personally identifiable information, and meeting patterns.
Learn more about how to keep video conferencing data secure.
Your data is your data
Compliance made easy
Compliance made easy
Stay in control of AI data
Privately and securely enable AI features for your video meetings, while keeping all training and input data within the borders of your organization. For industries under strict regulations and security requirements.
Certified by the strictest security standards worldwide
Pexip prioritized security from day 1. Because security can't be retrofitted.